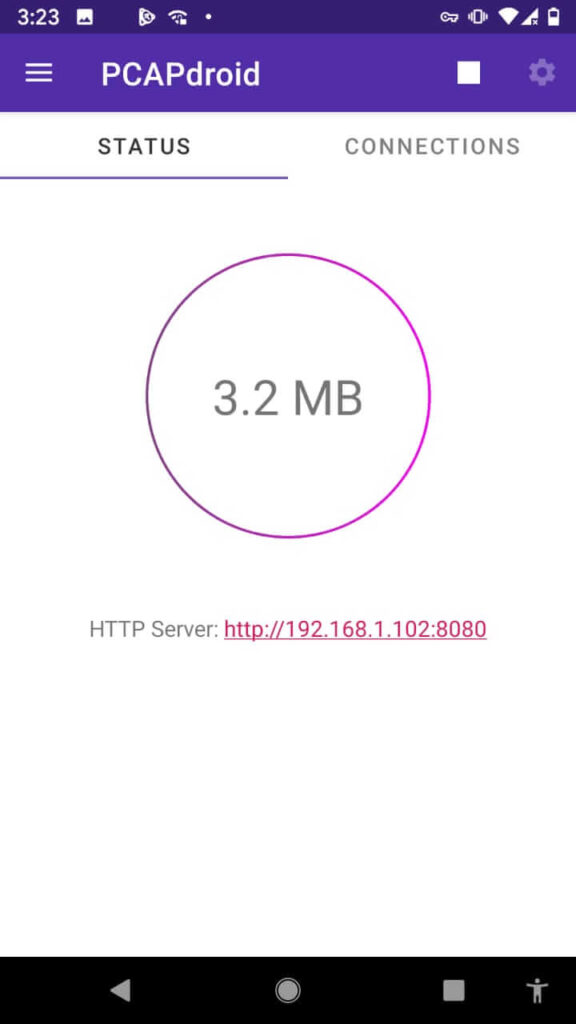
On the primary start, a VPN confirmation dialog is shown. After accepting it, PCAPdroid will start capturing the traffic. PCAPdroid is often put in the background while operating with the opposite apps because it continues to run as a service until the capture is stopped. As long as PCAPdroid is running, a key icon is going to be displayed into the android notification bar (this may vary counting on your system). Moreover, a persistent notification is shown, which incorporates the small print about the captured traffic.
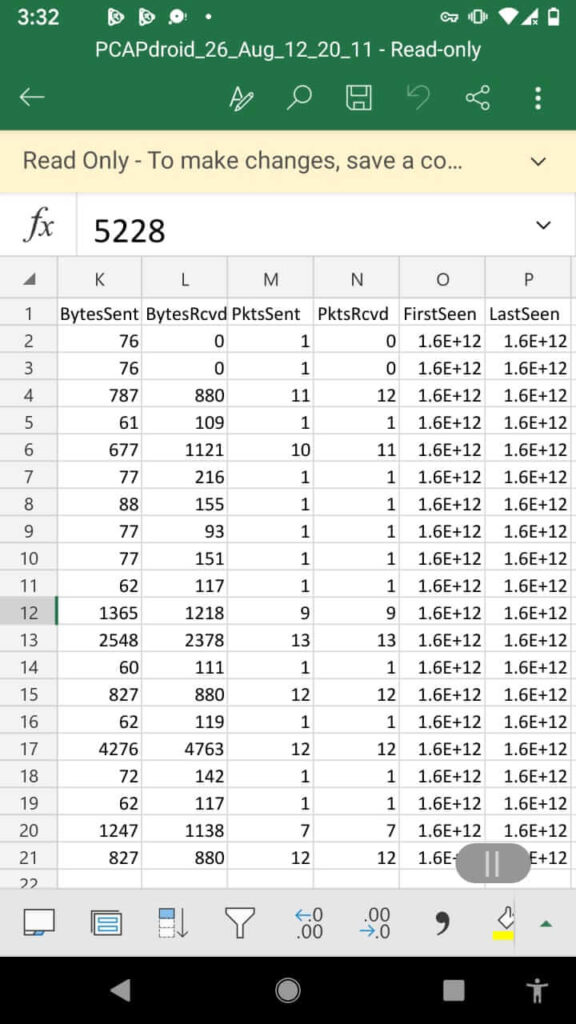
By default, an HTTP server is started on port 8080 to serve the traffic PCAP. you’ll visit the provided URL from another device (e.g. a PC) to start out downloading the PCAP. The download is streamed so it’s normal to ascertain a 0% download progress indicator within the browser.
Only the traffic generated after the download has been started are going to be captured. it’ll finish once the stop button in PCAPdroid is pressed. Beware that any user in your local network can download a replica of your device traffic! If you would like to avoid this, you’ll select “None” because of the dump mode.
Contents
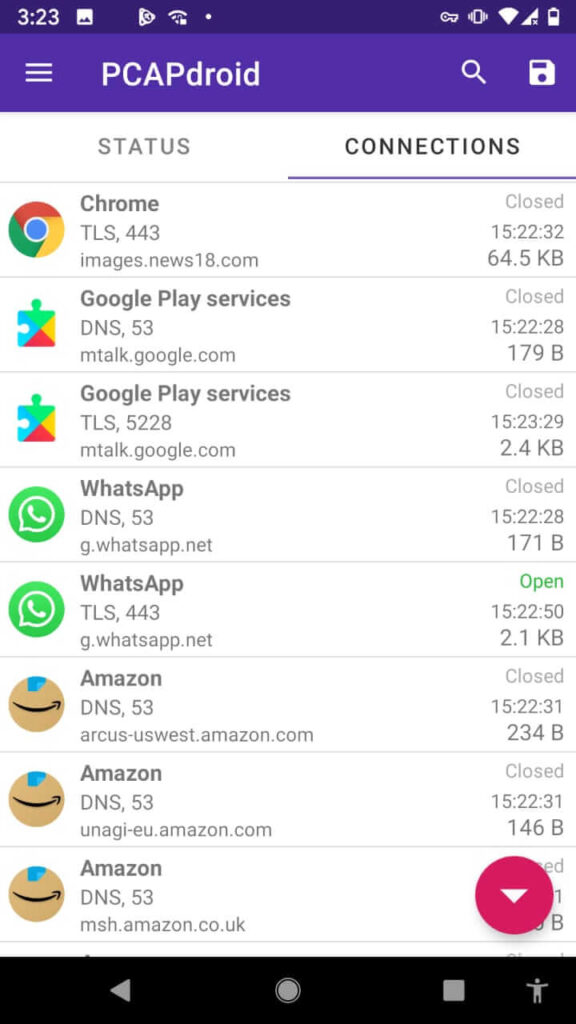
The connections made by the apps are often easily reviewed within the “Connections” tab. Each row represents an outgoing connection made by an app or by the android system itself. the subsequent information is shown:
- The app icon, or an issue mark if the app is unknown
- The app name
- The protocol of the connection, its port, and IP version (if not IPv4). this is often determined by analyzing the raw packets of the connection by using nDPI.
- The SNI (server name information) or DNS query, if available. Otherwise, the remote IP address.
- The connection status indicator, which may be “Open”, “Closed”, “Error”, or “Unreachable”.
- The last seen time, which is that the time of the foremost recent packet of the connection.
- The total traffic volume of the connection.
- By clicking on the connection it’s possible to urge more details about it.
- Some details, just like the IP addresses, status, and statistics, are always shown. Other information, just like the URL or the host, is merely shown when available. Among other things, PCAPdroid tries to detect the plain text request data sent at the beginning of a connection, which can be reported within the “Request Plaintext” row when available. For HTTP connections, for instance, it’ll show the HTTP request sent.
During the capture, PCAPdroid logs all the connections in memory. After a limit is reached, old connections are going to be removed and replaced by new ones, and a message indicating the amount of discarded connections is shown. a summary of the traffic generated by the apps is often seen within the “Apps” view.
By pressing on an app, its details page will open, where it’s possible to review its metadata, just like the installation date, version, and permissions.
By clicking on the “Settings” button, the system settings for the app will open. The “Connections” button provides a shortcut to point out the connections made by the app.
Before the capture is started, within the “Status” tab it’s possible to specify an “App Filter” to only capture the traffic of the required app. Only this app is going to be routed inside the VPN service. this is often especially useful when using the TLS decryption to make sure that the MITM will only happen on the target app.
After the capture is started, PCAPdroid provides alternative ways to filter the displayed connections:
via the search bar, it’s possible to filter the connections by IP address, host, protocol, app name, or did. A convenient thanks to searching the connections is by long-pressing a connection then selecting a filter from the contextual menu. from the Apps view, it’s possible to tap on an app to use it as a filter
by long-pressing a connection, it’s also possible to feature it to the whitelist The whitelist feature allows you to make rules to cover groups of connections from the “Connections” tab.
By carefully building a whitelist of “good” connections, it’s possible to filter the ground noise made by the periodic connections or by the frequently used apps and only display a couple of relevant connections. this is often particularly useful to detect unwanted or possibly malicious connections. The whitelist is persistent and may be modified from the corresponding entry within the left drawer.
PCAPdroid is an open-source network monitoring and capture tool. It can capture Android device traffic without rooting the device. The traffic can be sent to a remote receiver.
Features:
– Log and examine the connections made by the user and system apps
– Extract SNI, DNS query, HTTP request, HTTP URL, and remote IP address
– Apply a filter to only capture the traffic of the selected app
– Easily download a PCAP file of the traffic thanks to the integrated HTTP server
– Stream the PCAP to a remote receiver for further analysis (e.g. Wireshark)
– Decrypt HTTPS/TLS traffic via a remote mitmproxy
– On rooted devices, it can capture the packets while other VPN apps are running.
Important: the PCAP generated by PCAPdroid is not 100% accurate. Check out PCAP Reliability for more details.
One more thing that I think I should share with you can check out this – Best Sound Amplifier App For Android Device
PCAPdroid leverages the Android VpnService to receive all the traffic generated by the Android apps. No external VPN is actually created, the traffic is locally processed by the app. Visit the project’s Github repo for more details.
Download PCAPdroid – no-root network capture